System Vulnerabilities
Is LiquidFiles vulnerable to CVE-YYYY-XXXX?
Please enter the CVE number in the Ubuntu CVE database: https://ubuntu.com/security/cves to see if Ubuntu is vulnerable to a specific CVE number. If/when Ubuntu releases an update, it will be made available to all Ubuntu systems, including LiquidFiles. LiquidFiles uses Ubuntu 22.04LTS (Jammy).
Regardless if LiquidFiles is currently vulnerable or not, the only thing you can do is to enable automatic system security updates to stay protected.
Is LiquidFiles vX.Y.Z vulnerable to Heartbleed, Shellshock, CVE-YYYY-XXXX?
If you have enabled automatic system security updates but haven't updated LiquidFiles, you may well be running an older version of LiquidFiles and still be up to date on system security patches. When you update to a new version of LiquidFiles, it will always install the latest operating system functions.
This means that it's impossible to say what version of a system function like OpenSSH or OpenSSL is installed on your specific LiquidFiles system because it will depend on when you installed it and if you have enabled automatic system security updates.
Enable automatic System Security Updates
The only thing you can do to stay protected long term is to enable automatic system security updates in Admin → System → Updates. This is the default and recommended setting:
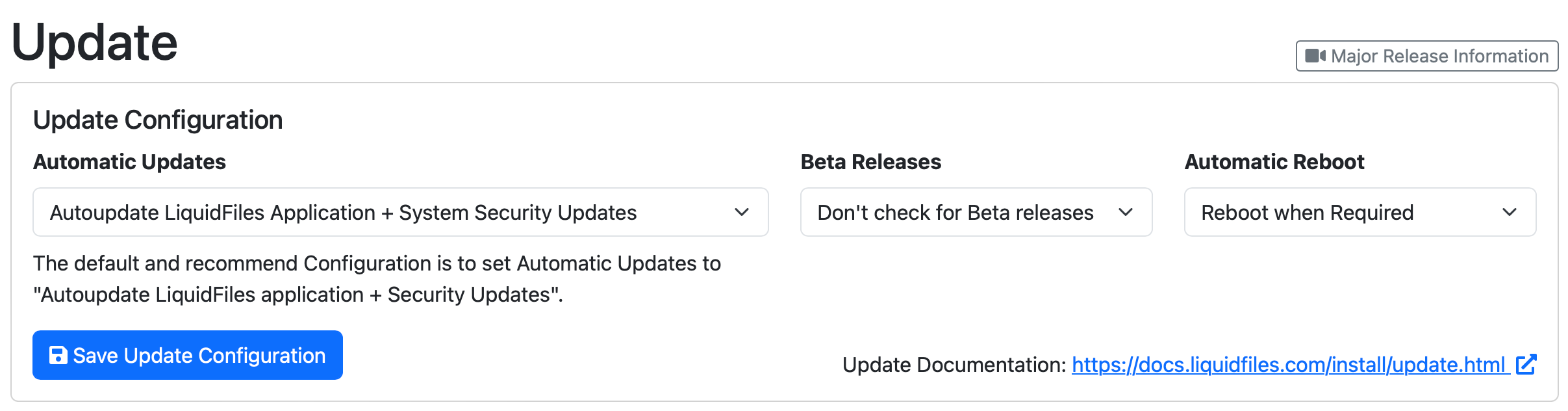
This will ensure that your system is up-to-date with the latest application and security updates and is the safest way to run LiquidFiles. When Ubuntu releases security updates, they will be installed nightly. LiquidFiles application updates will be installed about a week after an update has been released to give extra protection should an issue be detected shortly after release.
Manual Patching
Every so often we get a question along the lines of "my scanner has reported that the installed OpenSSH version is older than what my scanner thinks it should be, can I just manually install a new version?"
No. If you manually install a version from source, you are almost guaranteed to break the system beyond rescue and the only way forward would be to reinstall LiquidFiles and restore from a backup. All Linux vendors, including Ubuntu (and CentOS that we used in earlier releases) include many operating system specific tweaks to their installations and also manually patch versions without necessarily update the version to a later release. In other words, an older version may not be vulnerable just because your scanner think it is. In order to see if the system is vulnerable, you have to check the CVE database as outline above, and the only thing you can do is to enable automatic updates outline above.
