Automatic Assignment of Users to Groups
LiquidFiles is built to be self administrating as far as possible. When it comes to user management, the easiest way to deal with users is to divide users into groups and use automatic group assignments to assign users into different groups.
When assigning users, users are matched in the following order:
- If the user is found in LDAP and has a group that match any of the listed LDAP groups, assign the user to that group. If the user belongs to several groups, the user will be assigned to the first listed group.
- If the user is found in LDAP but does not belong to any of the listed LDAP groups, assign the user to the default group for LDAP users.
- If the user is not found in LDAP and has an email address that match any of the listed matched email domains, assign the user to that group. If the user has an email address that match several domains, assign the user to the first listed group.
- If the user is not found in LDAP but matches any of the Local Domains, assign the user to the default group for Local Users.
- If the user is not found in LDAP and does not have an email address that match any of the listed email domains or Local Domains, assign the user to the Default Fallback Group.
Default Group Assignment
You can change the default automatic Group Assignment in Admin → Groups, in the Default Group Asssignment tab. It will look similar to the screenshot below. With this configuration, you can adjust the fallback settings for LDAP authenticated users, SSO (SAML2) authenticated users, users in Local Domains and everyone else that's not already matched.
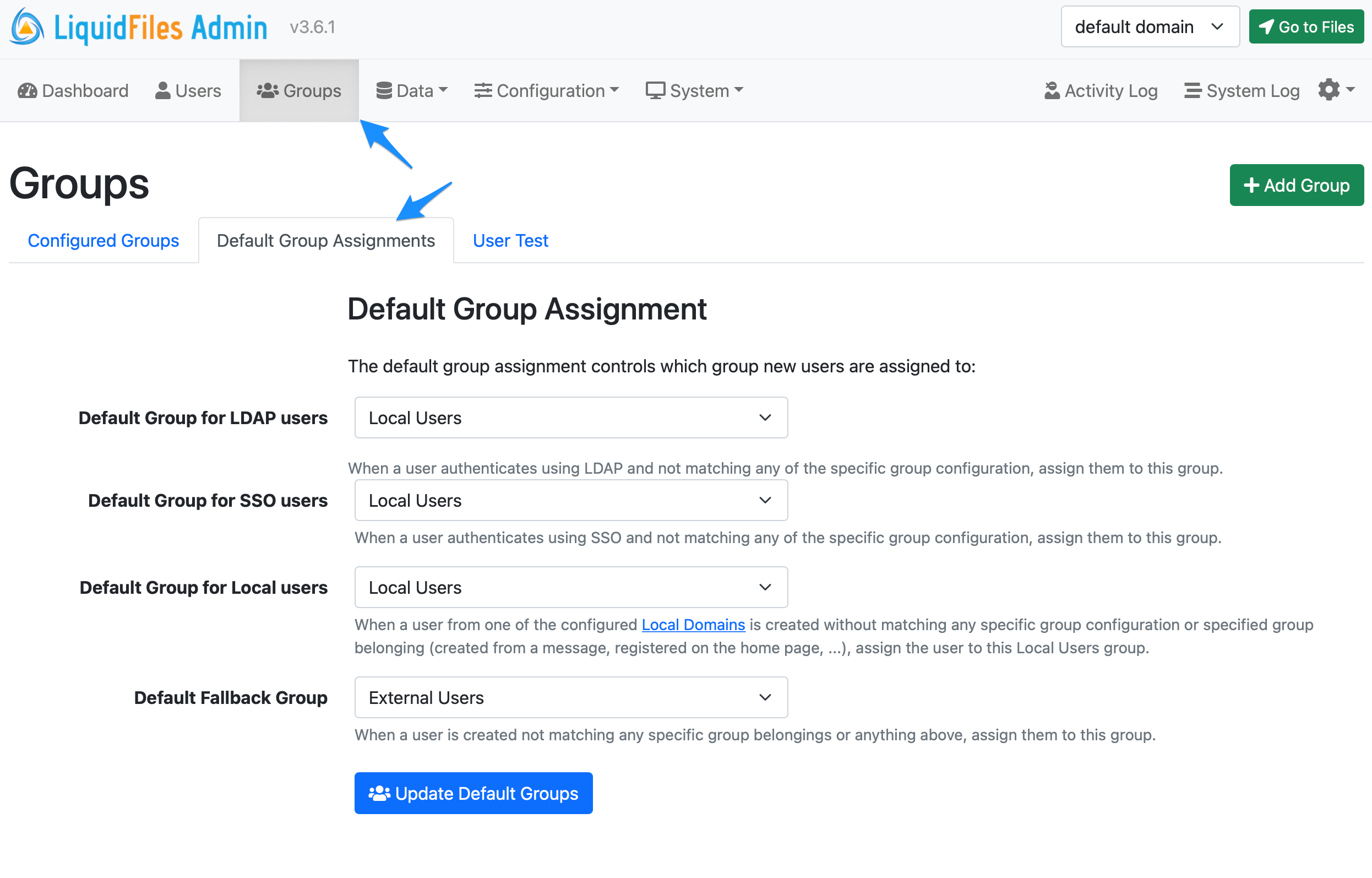
Group Matching
When you edit a group and look in the Assignment tab, you can see different options for matching users to this group.
In the screenshot below, if a user logs in to this LiquidFiles system and belongs to a LDAP/AD Group LiquidFiles Users, they will be assigned to this group.
Same if a user login to this system using SSO/SAML2 and the SAML server responds with an extra attribute "memberOf" and memberOf is LiquidFiles Users, the user will be assigned to this group.
Finally, if a user registers on the front page of this LiquidFiles system and their email address matches @ourcompany.com or @ourotherbrand.com, they will be assigned to this group.
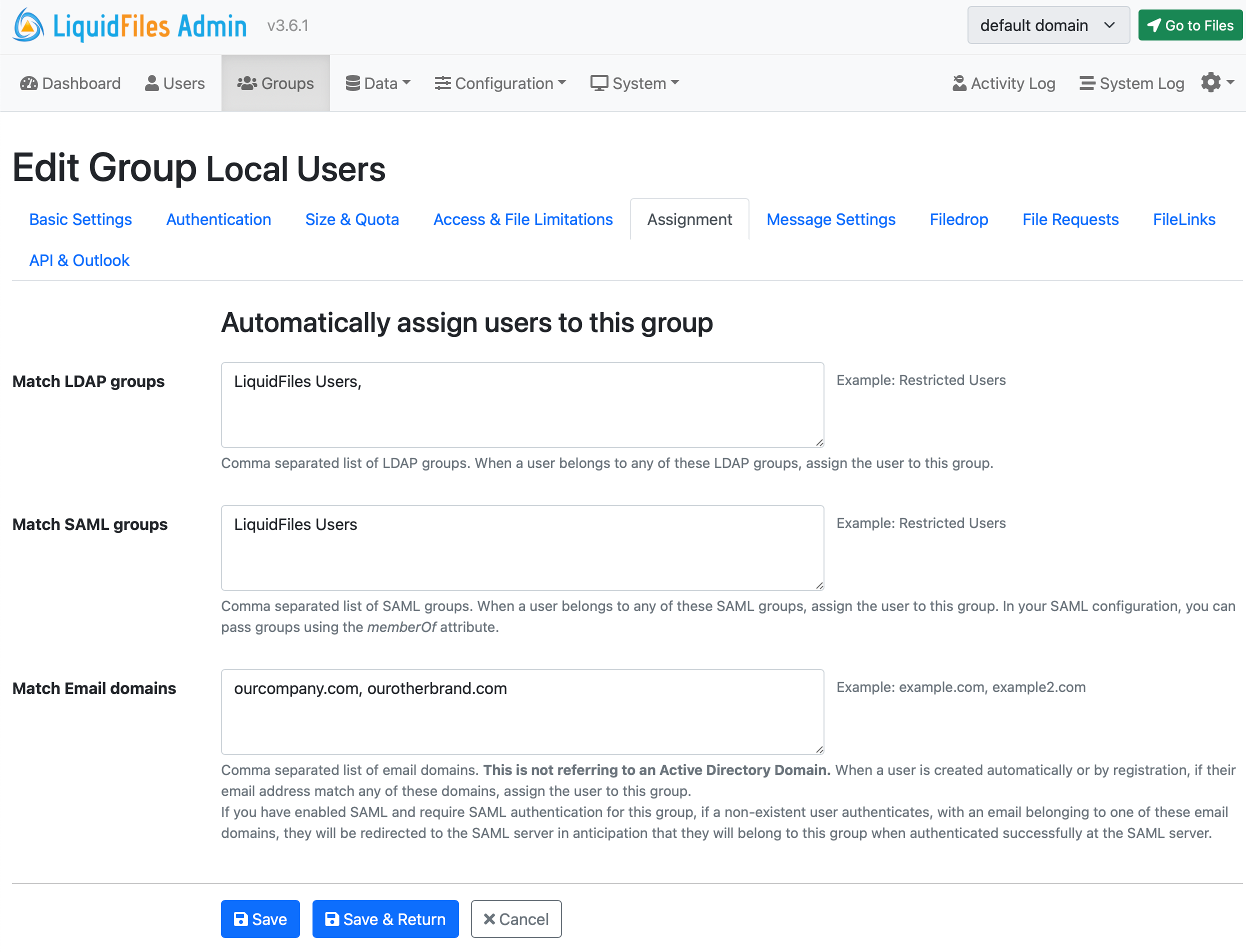
The main benefit of using group matching is when you create your own custom groups and you want to have for instance a different local user group for the marketing department with different group configuration from the default Local Users group and similar.
Locking Users to Groups
By default, the group matching is performed every time a user logs in to the LiquidFiles system. If you create a new LiquidFiles group Local Users XL that can send up to 1000GB files, vs your default Local Users group can send max 1000MB files, and then create an LDAP group LiquidFiles Users XL and match this new LiquidFiles group, and then drag the Local Users XL group above the Local Users group so that the configuration looks like this:
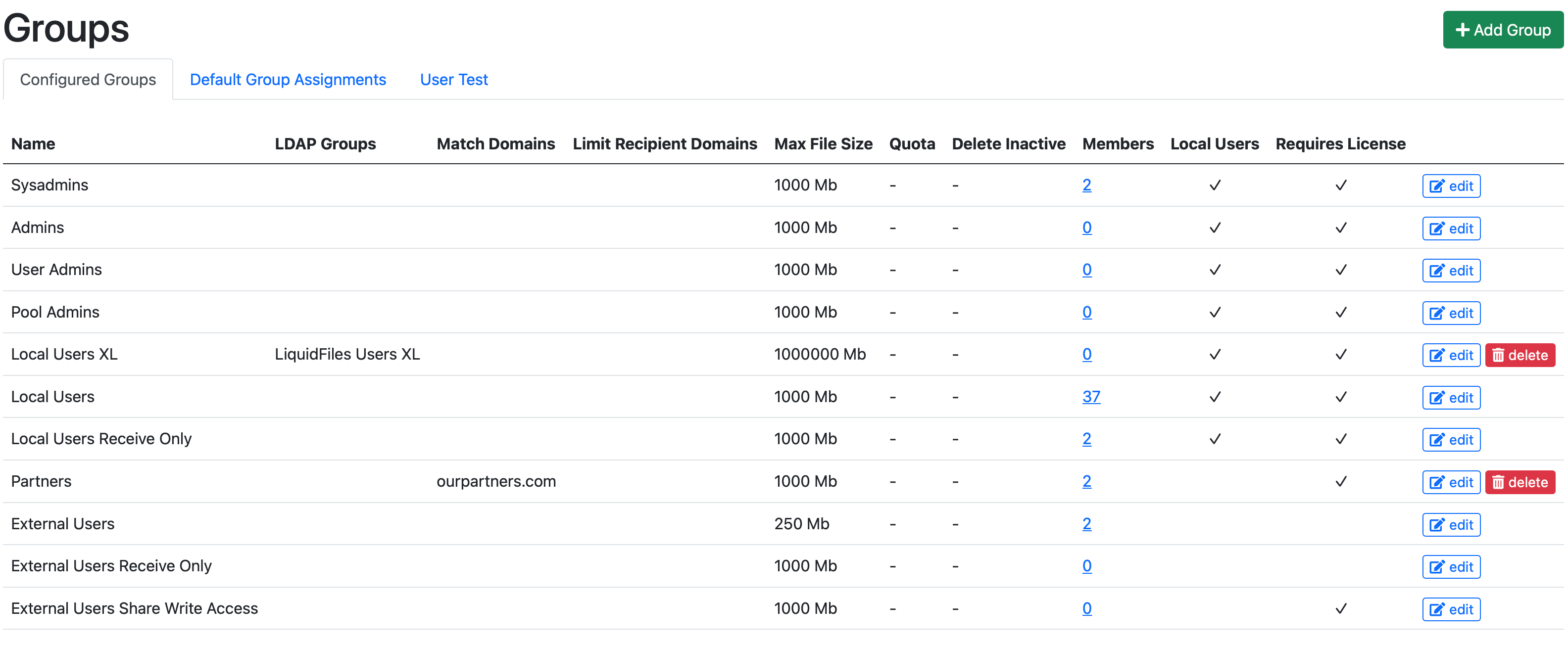
If you have a user and you want to give them access to the Local Users XL group, you update their group belongings in your LDAP/AD group and add them to the LiquidFiles Users XL group. Next time they login, this user will be reassigned to the Local Users XL group.
Alternatively, you can add specific users to the Local Users XL group manually in Admin → Users:
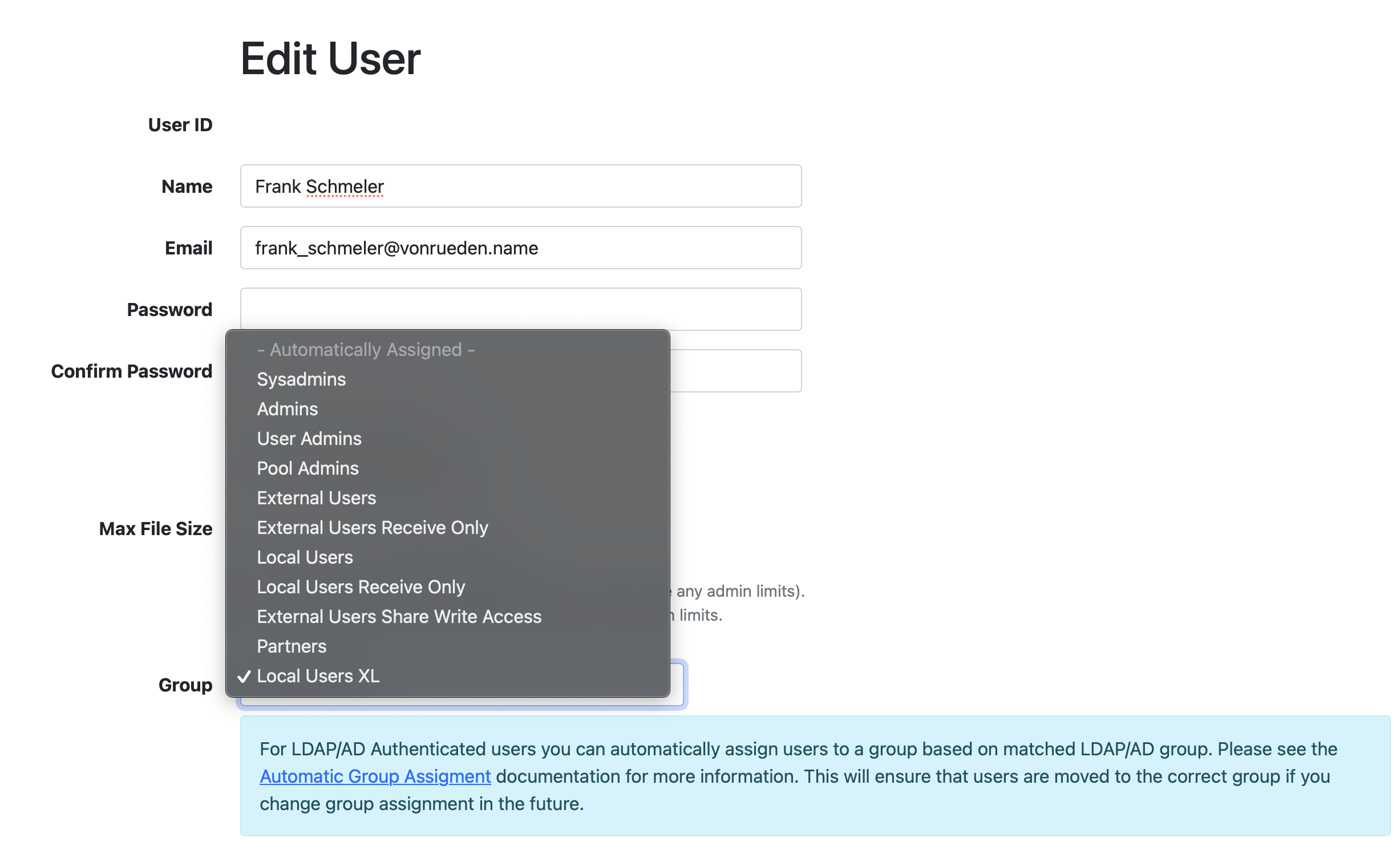
On default, users are created with the - Automatically Assigned - setting, which will automatically assign users to different groups as the configuration change. And any user with a specific group setting configured will keep that group regardless of other group matchings that's been configured or updated.
System Administrators
Please Note that System Administrators will never be moved out of the System Administrators group regardless of configuration. This is a safeguard to ensure that the System Administrators you configure will stay configured as System Administrators. If you wish to demote a user from System Administrators to another group, you will need to do this manually.
Example
If we look at an example system (https://liquidfiles.company.com), we can see the following Admin → Groups configuration:
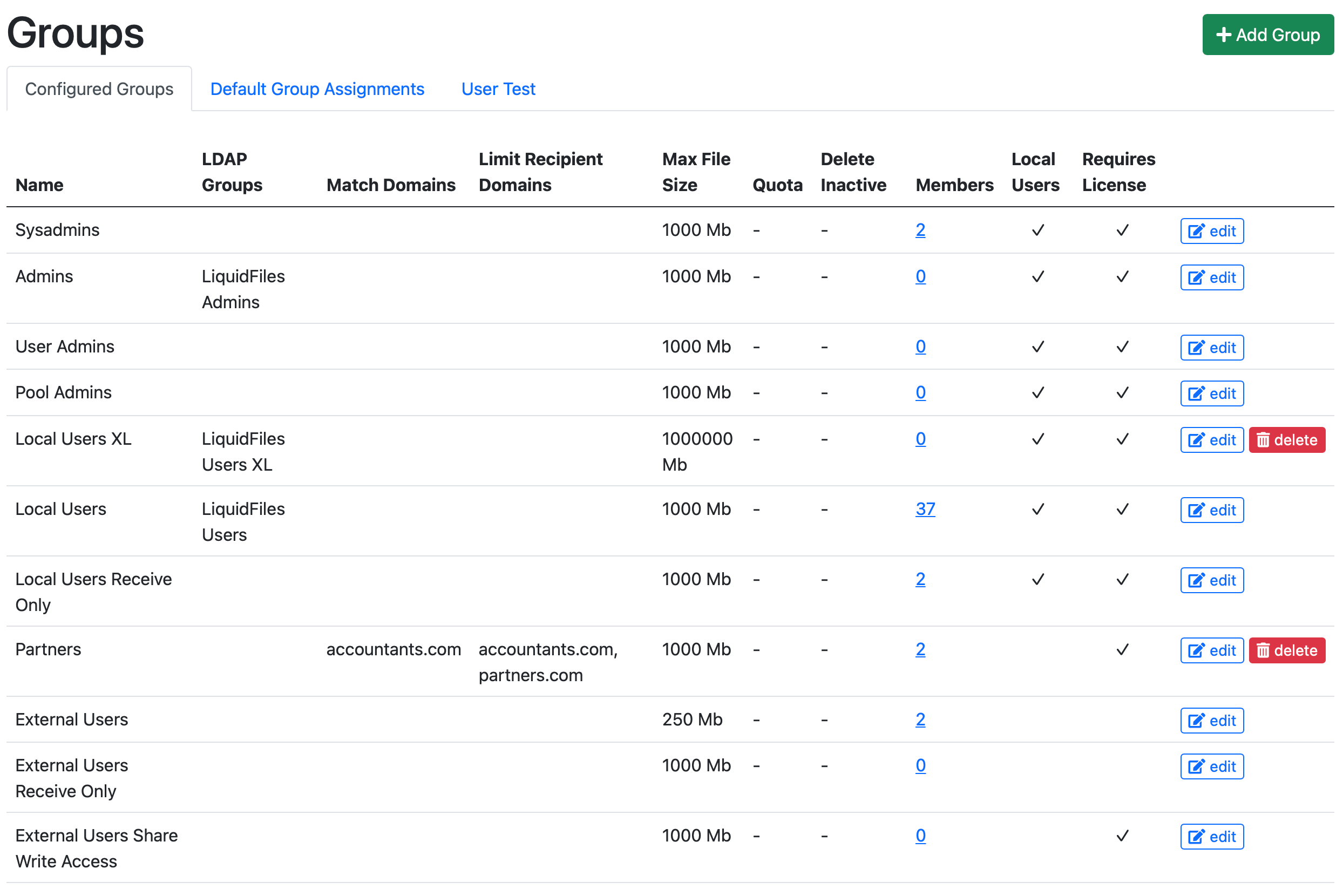
With the following Default Groups configured
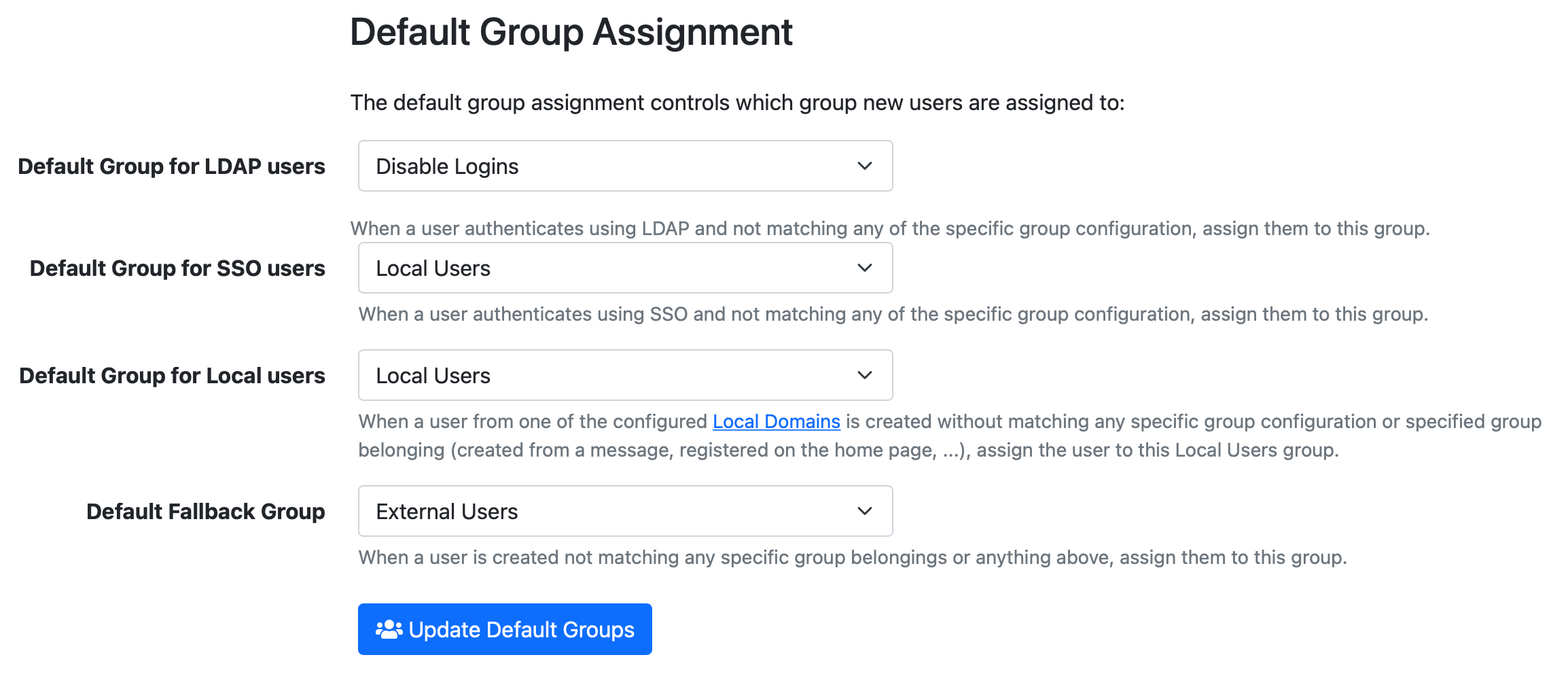
The configuration in this example would be:
- There's no automatic assignment of Sysadmins.
- Users in the LDAP/AD group "LiquidFiles Admins" will be automatically assigned to the Admins Group.
- User Admins and Pool Admins are not used in this company.
- The Local Users XL group is a group that is assigned from the LDAP/AD group LiquidFiles Users XL and enables users in this group to send larger files.
- Local Users are automatically assigned from the LDAP/AD Group LiquidFiles users.
- Local Users Receive Only are only assigned by manually adding users to this group.
- Next is the "Partners" group, which is quite interesting. users with an email domain @accountants.com will be automatically assigned to this group when they register or create an account. Users in this group can only send messages to users in the email domains accountants.com and partners.com.
- External Users can only send to the Local Domains.
- Nothing really to note about the Externl Users Receive Only group or External Users Share Write Access.
- Any LDAP User that doesn't belong to either the LiquidFiles Admins, LiquidFiles Users XL, LiquidFiles Users, or have been manually added to this system (a Sysadmin for instance can still authenticate with LDAP), will not be able to login to this system — Default Group for LDAP users: Disable Login.
Testing Group Assignments
If you have a lot of groups with lots of matching going on, it can quickly become difficult to get a complete overview exactly what will happen. In order to make testing this easier, there's a User Test function in the User Test Tab the Admin → Groups page.
By entering whatever the user would type on the login page, you can test what would happen.
Here are a couple of examples:
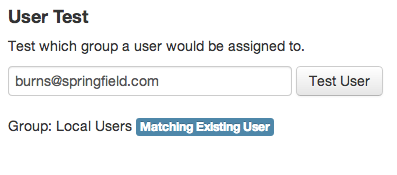
Here we can see that: burns@springfield.com, is an already existing user in the local users group.
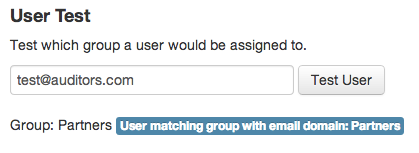
If anyone with an email address in the domain: @auditors.com, they would be assigned to the "Partners" group.
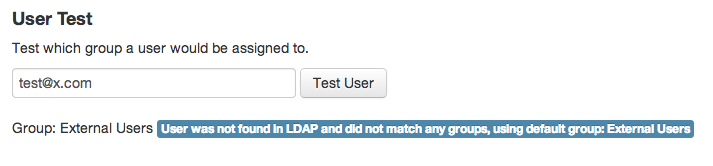
In this case the email address does not match any existing user and does not match any existing email domain, they would be assigned to the default group for non-ldap users: External Users.
And so on. Please make sure that you test thoroughly so that all users are assigned to the correct groups.
